Deepfake Videos & Deephot Link Explained: What You Need To Know
Could the very fabric of our digital reality be unraveling before our eyes? The proliferation of deepfakes and manipulated content presents a significant challenge to trust and authenticity in the digital age, forcing us to re-evaluate what we perceive as real and the impact on our societal and personal safety.
The digital landscape is perpetually evolving, with technological advancements occurring at a dizzying pace. Among the most intriguing, and often unsettling, innovations is the rise of "deepfakes" videos created using artificial intelligence to replace one person's likeness with another's, and the deep hot link website, a concept rapidly gaining momentum due to its potential to redefine how we navigate the web. Simultaneously, the ease of access to content of questionable origin continues to grow. The implications of this convergence are profound, touching upon areas from personal privacy to geopolitical stability.
But what, precisely, is a deep hot link website? Before we delve into the complexities of this emergent technology and the challenges it presents, let's first examine the components that make up a link, a fundamental element in this digital puzzle. Understanding the building blocks is essential.
The anatomy of a link, whether deep or otherwise, always comprises the authority and hostname, the foundational elements that direct your browser to the intended destination. The authority specifies the protocol (e.g., HTTP, HTTPS) and the hostname, the domain name or IP address where the resource resides.
Consider the implications of manipulated content. While entertaining in some instances, the ease with which someone's image or voice can be altered raises serious ethical and security concerns. The potential for misinformation campaigns, reputational damage, and even financial fraud is undeniable. As technology advances, so too must our awareness of these risks. We must develop critical thinking skills and learn to identify telltale signs of manipulation. This requires a multi-faceted approach, involving education, technological solutions, and legislative frameworks.
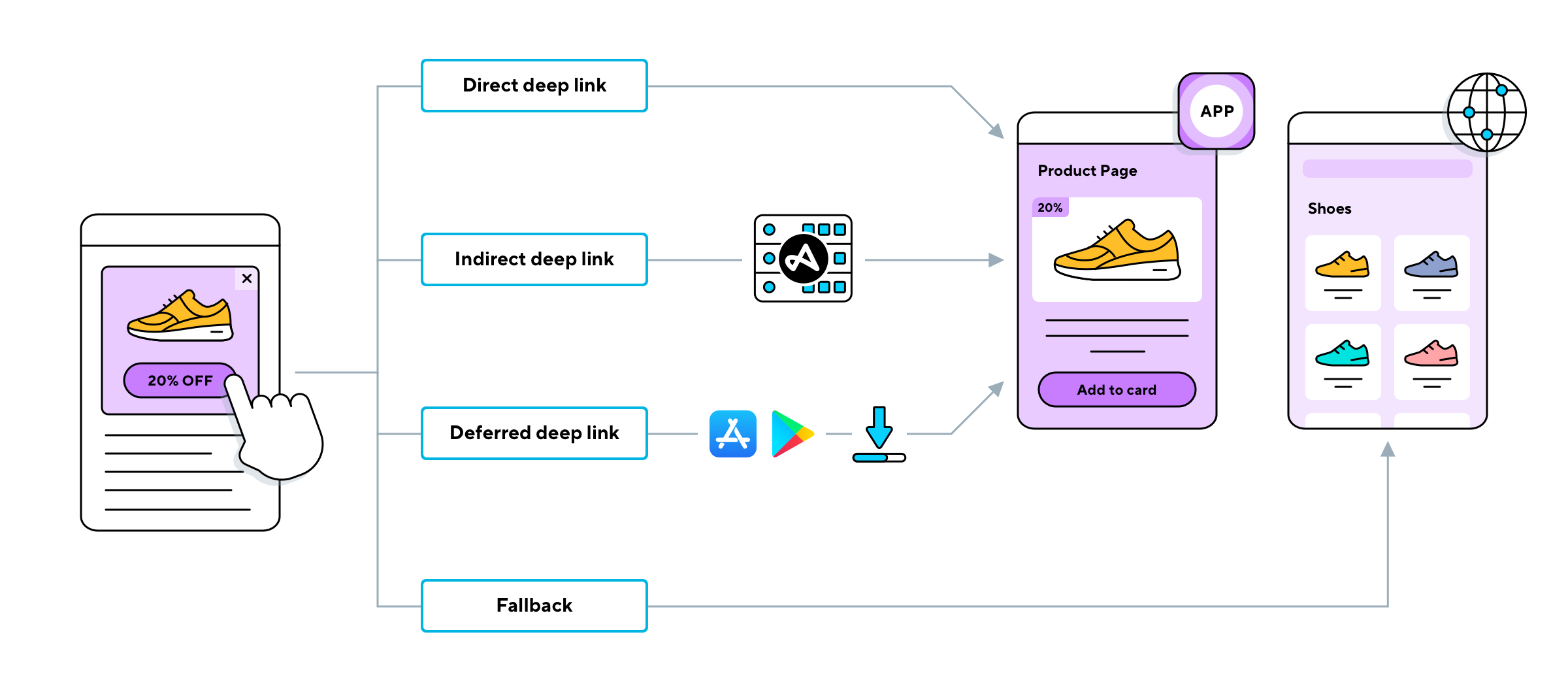
The creation of a "deep link" url is a process of strategic engineering. This is where deep linking platforms and specialized libraries become invaluable tools, they allow for the creation of unique URLs that can be tailored for precise navigation within an application or website. After the destination has been determined, one must generate the link. This is often where analytical and tracking parameters are added for analysis.
The next essential step is adding the deep link into the codebase, seamlessly integrating it into the application's underlying structure to unlock the desired functionality.
In the realm of online content, the availability of deepfake porn videos is a concerning development. These videos, often featuring celebrities or public figures, exploit the power of AI to create explicit content that can be used for malicious purposes, potentially leading to defamation, harassment, and severe emotional distress for those involved. The ease with which such content can be created and distributed online poses a significant challenge to individual privacy, and the need for stringent regulations and technological solutions to combat this issue is urgent.
Password reset mechanisms are a fundamental aspect of online security, providing users with a way to regain access to their accounts. A password reset link, sent to a user's registered email address, allows them to securely change their password and protect their personal information. This process is an essential tool for managing account security in the digital world.
Let's now explore the potential of the "deephot link" and the possibilities this emerging technology offers.
The deephot link website introduces an intriguing innovation, particularly in photography. Imagine an interactive visual experience where viewers can explore images in unprecedented detail. This technology holds the potential to revolutionize how photographers showcase their work, offering an immersive, engaging experience that transcends traditional presentations.
With deephot link, photographers can unlock new creative dimensions, showcasing their work in stunning detail and engaging viewers like never before. By choosing deephot.link, users can take control of their digital lives and browse the internet with confidence. We encourage you to try deephot.link today and experience the benefits of secure and anonymous browsing. Don't forget to leave a comment below sharing your thoughts and experiences with the platform. By staying ahead of industry trends, deephot.link ensures that its users are always equipped with the latest tools to succeed in their digital endeavors. Deephot.link is a link management platform that allows users to create custom URLs, track performance metrics, and integrate with other tools to streamline workflows.
In the wake of this, the rise of deepfake technology raises questions.
The creation of convincing forgeries is not confined to the manipulation of images and videos. Deepfakes can also be used to generate audio mimicking the voices of others, and the impact of these new advancements on various facets of society demands careful consideration. Misinformation can spread through this method. The use of deepfakes will be more frequent over time and requires action.
In the context of internet security, users should be vigilant and aware of the risks. Secure and anonymous browsing is essential, the ability to browse freely and avoid surveillance is crucial for individual safety. With its commitment to user privacy, Deephot.link encourages people to browse safely.
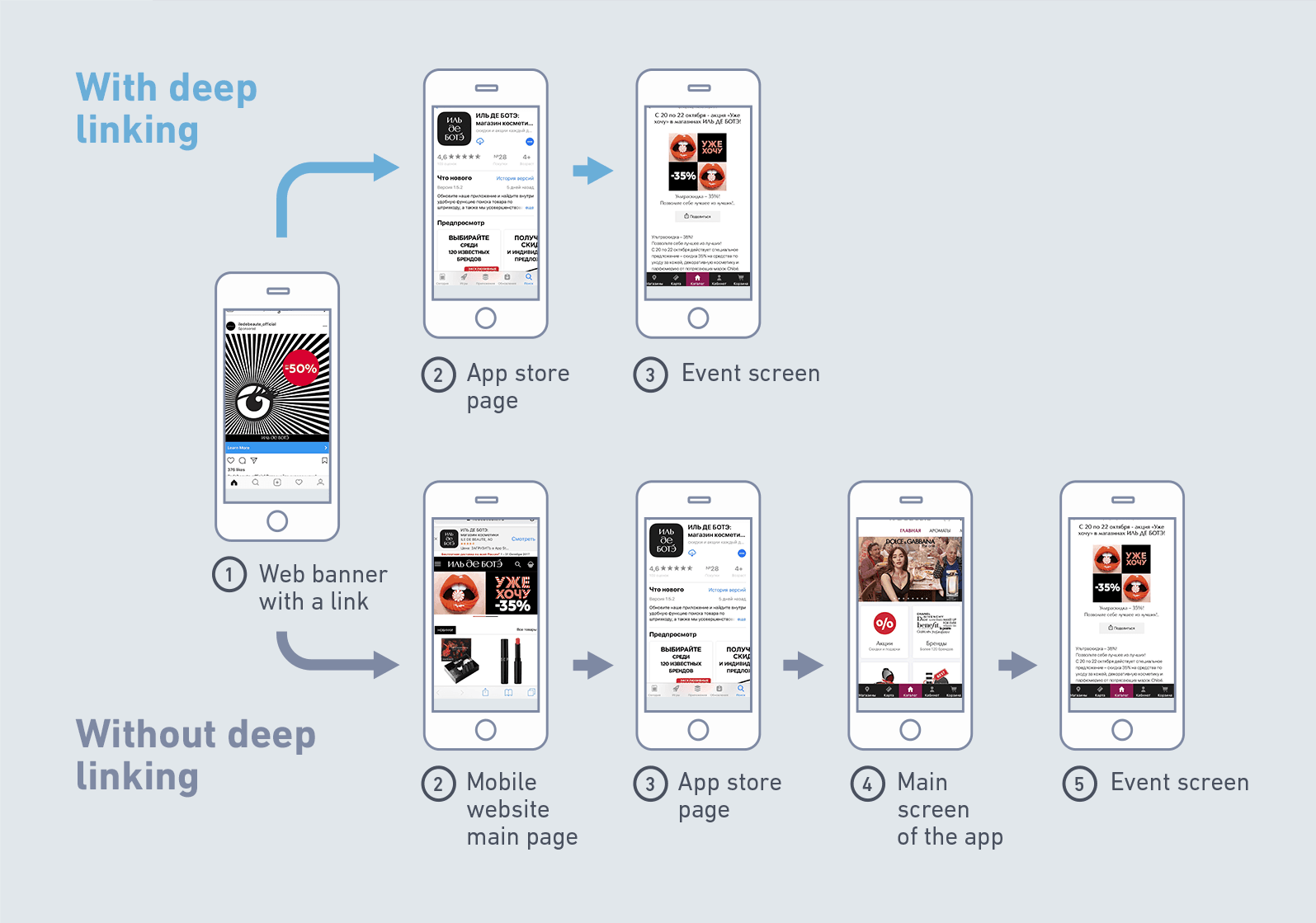
Deep linking is a concept critical to understanding the functions and nuances of web pages.
Navigating the complex world of digital content requires a solid understanding of deep linking. This technique allows you to send users directly to specific content within an app or website, eliminating the need for them to navigate from the homepage. The advantages of deep linking are clear: enhanced user experience, increased engagement, and more effective content delivery.
The process involves creating a custom URL using a deep linking platform or library to redirect users to a specific destination. Tracking and analytics are often integrated for enhanced performance.
The potential uses of deep linking extend far beyond convenience. They present opportunities for targeted advertising, customized user experiences, and improved content discovery. The importance of these technologies will only increase as the web continues to evolve, and so will the need to comprehend how to harness their strengths to our benefit.
Its essential to implement digital tools which will maintain a balance between information access and user safety.
The world of digital content is at a critical juncture. Developments like deepfakes and the ability to swiftly manipulate information raise legitimate concerns, but tools like deep linking also hold great promise. As the field advances, it is essential to adopt a balanced approach: embracing the benefits of innovation while mitigating the associated dangers, through education, vigilance, and thoughtful regulation. By being informed and proactive, we can shape a digital future that is both dynamic and safe.
It is important to consider the role of ethical considerations in this expanding digital terrain.
The rise of deepfake porn is an example of what happens when technology is misused. It is critical to be aware of the ethical ramifications of digital content and to promote a culture of responsibility. Promoting education in digital literacy is more critical than ever in this new world.
The ability to remotely access and control a computer from anywhere is a game-changer in today's digital age.
Connecting to any computer, at any time, offers a level of flexibility and convenience that was once unimaginable. Whether for work, personal use, or technical support, the ability to remotely access a device empowers users and boosts productivity. With the availability of free tools to assist with these functions, it is now easier than ever to integrate remote computer access into your daily life.