Telegram Groups & Channels For IP Cam: Find & Join Now!
Is the world of networked cameras truly as secure as we believe, or are we unknowingly leaving ourselves vulnerable to prying eyes? The proliferation of "ipcam" related groups and channels on platforms like Telegram suggests a darker reality, where privacy is a commodity and surveillance is a click away.
The digital landscape has become a breeding ground for activities that exploit vulnerabilities in interconnected devices. While the concept of smart homes and remote monitoring offers unparalleled convenience, it simultaneously introduces potential risks. The information below exposes some of the ways that "ipcam" groups on platforms like Telegram operate.
Let's delve deeper into the world of "ipcam".
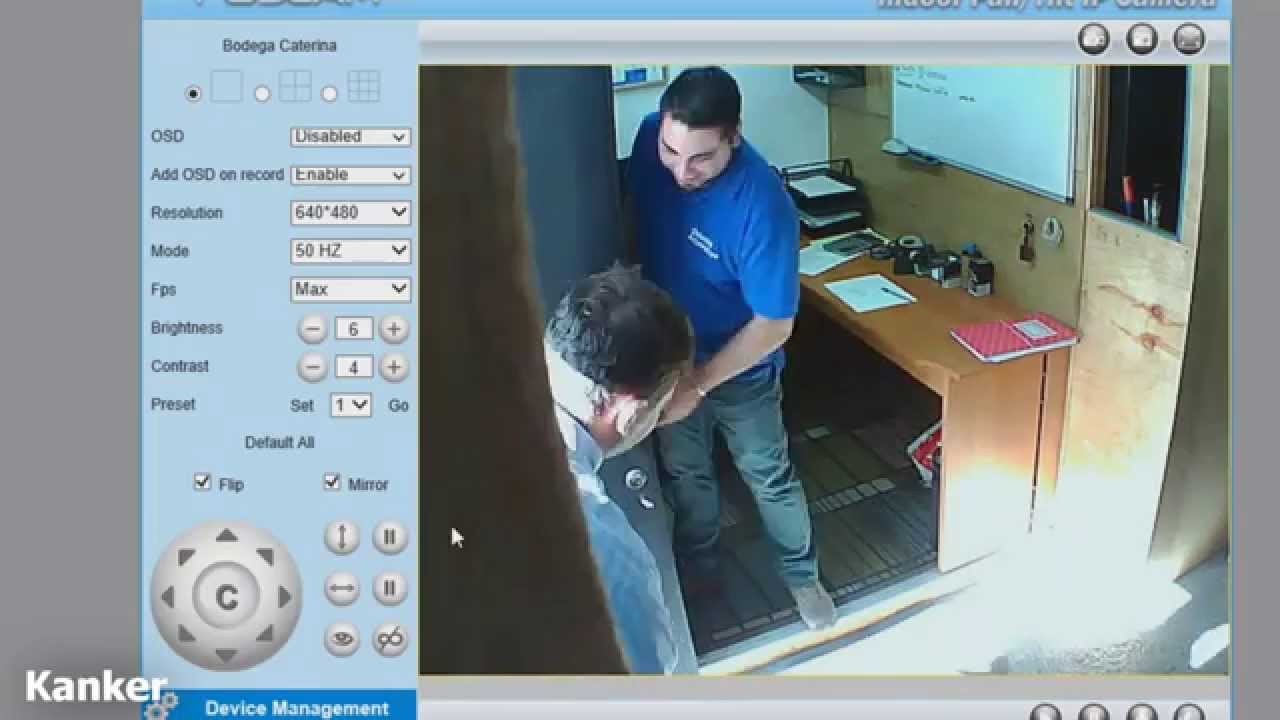
The digital age has ushered in an era of unprecedented connectivity. From smart refrigerators to sophisticated security systems, the Internet of Things (IoT) has become an integral part of our lives. Among these connected devices, Internet Protocol cameras, or "ipcams," have emerged as a cornerstone of modern surveillance. They offer the ability to monitor homes, businesses, and public spaces remotely, providing a sense of security and peace of mind. However, the convenience of ipcams comes with a significant caveat: security vulnerabilities. The very features that make these devices so appealing also make them potential targets for malicious actors.
One of the primary concerns surrounding ipcams is the lack of robust security measures. Many devices are shipped with default usernames and passwords that are easily guessable or readily available online. This leaves them open to unauthorized access by anyone with the right technical skills. Furthermore, some manufacturers fail to provide timely firmware updates to address security flaws, leaving their products vulnerable to exploits for extended periods. These lapses in security are often compounded by user negligence. Many individuals fail to change the default credentials, leaving their devices exposed to potential compromise. Even when users do update their passwords, they often opt for weak or easily guessable combinations, further increasing the risk of unauthorized access.
Once an ipcam has been compromised, the potential for abuse is extensive. Attackers can gain access to live video feeds, allowing them to observe activities within a home or business. They can also record and store video footage, potentially using it for blackmail, extortion, or other malicious purposes. In some cases, attackers may even be able to control the camera's pan, tilt, and zoom functions, allowing them to monitor specific areas of interest. Beyond the direct privacy violations, compromised ipcams can also be used as a gateway to the broader network. Once an attacker gains access to a device, they can potentially use it to launch attacks against other devices on the same network, including computers, smartphones, and other connected devices. This can lead to data breaches, identity theft, and other serious consequences.
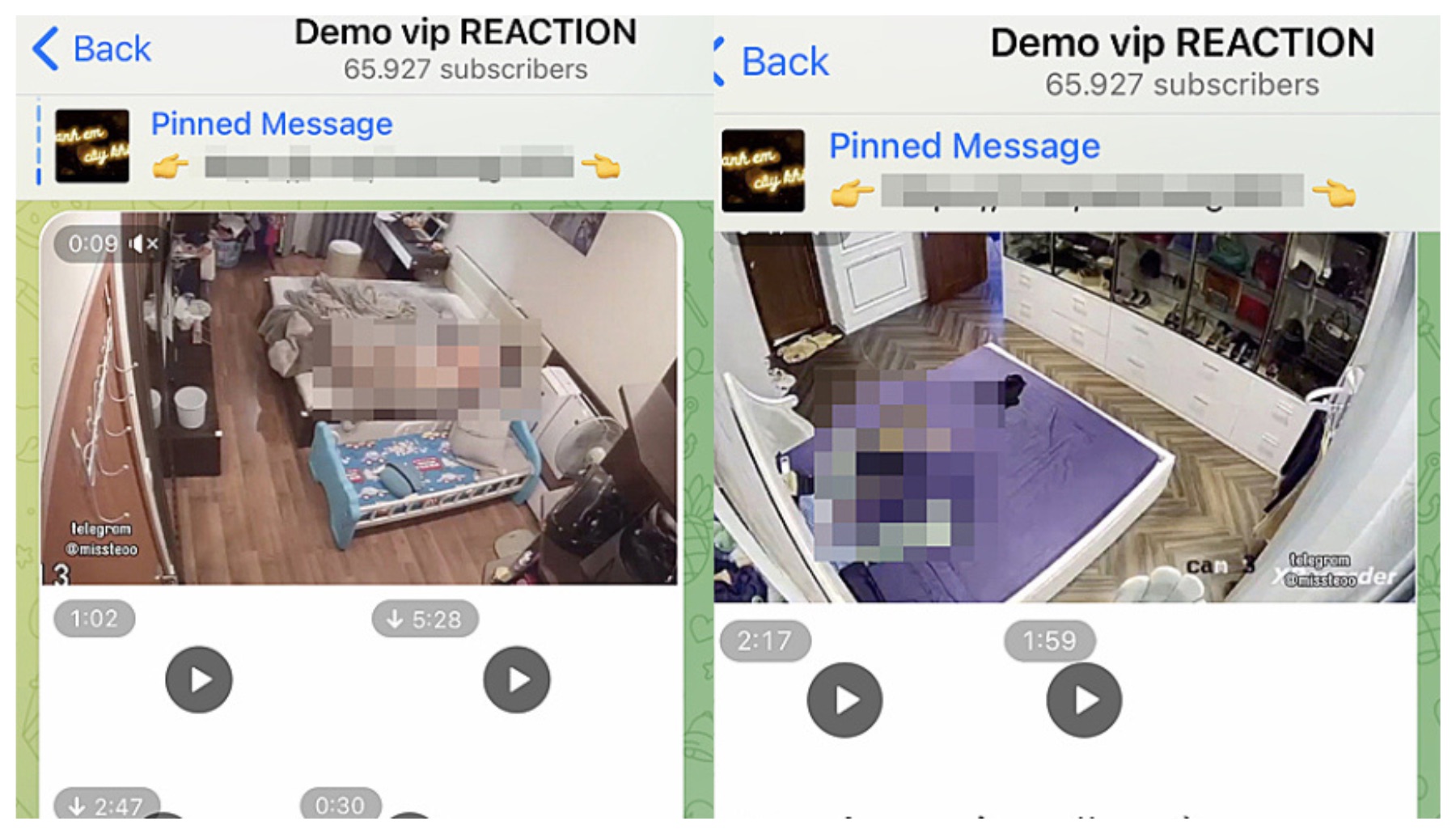
The proliferation of online platforms such as Telegram has further exacerbated the problem. These platforms offer a haven for individuals and groups seeking to share information about compromised ipcams. These groups frequently post links to live video feeds, offer instructions on how to access vulnerable devices, and share lists of known vulnerabilities. The anonymity provided by these platforms makes it difficult to track down and prosecute individuals involved in these activities. This, in turn, encourages further exploitation and perpetuates a culture of disregard for privacy. The ease with which one can find and join these groups is concerning, highlighting the urgent need for increased awareness and proactive security measures.
The ecosystem is teeming with groups and channels dedicated to "ipcam" related content. These entities are often organized around specific themes or niches, ranging from accessing live feeds to sharing information about specific vulnerabilities. Some focus on providing tutorials or instructions, while others simply share links to compromised cameras. A notable aspect is the use of Telegram's features to facilitate distribution and communication. The platform's channels allow for broadcasting information to a large audience, while groups foster interactive discussions and the exchange of information. The speed at which new groups emerge and the constant evolution of their tactics presents a significant challenge for security professionals and law enforcement agencies.
One of the critical aspects of addressing this issue is education. Individuals need to be informed about the risks associated with ipcams and the steps they can take to protect themselves. This includes using strong, unique passwords; regularly updating firmware; and disabling remote access features when they are not needed. Awareness campaigns can play a vital role in educating the public about these critical security best practices. Another is promoting the adoption of security standards by manufacturers. Implementing robust security measures by default will significantly reduce the number of vulnerable devices and make it more difficult for malicious actors to gain unauthorized access. Governments and regulatory bodies can play a role by establishing and enforcing security standards for all connected devices. Collaboration between device manufacturers, security researchers, and law enforcement agencies is also crucial. Sharing information about vulnerabilities and coordinating efforts to identify and neutralize threats can significantly improve the overall security posture of the ecosystem.
The ongoing battle to secure ipcams is a multifaceted challenge. It requires a combination of technical solutions, user education, and legal and regulatory frameworks. While the convenience of remote monitoring is undeniable, it is essential to recognize and address the associated risks. By taking proactive steps to improve security, we can protect our privacy and ensure that the benefits of connected devices outweigh the potential dangers.
Within these digital enclaves, the exchange of information related to ipcams is frequent. The focus often revolves around the exploration of links to various communities, supergroups, and chats. This decentralized network of information sharing presents a complex environment where privacy can be compromised.
The landscape of telegram groups and channels related to ipcam is extensive, and often categorized by content type, such as family, or by functionality. Within the search results, there are tabs dedicated to different types of content. One tab contains all the channels matching specific criteria; another shows the groups, and yet another contains the bots associated with the "ipcam" topic. Each item listed in these tabs is ordered by its relevance to the search query. This arrangement provides users with a systematic way to discover and engage with the various aspects of "ipcam" groups and channels.
The following table provides a compilation of key details pertaining to the ecosystem of "ipcam" related groups and channels found on platforms like Telegram, offering a glimpse into the organizational structure and thematic focus of these online communities.
| Category | Description | Examples |
|---|---|---|
| Channel Purpose | The primary function or intended use of the channel or group. | Sharing live feeds, providing hacking tutorials, exchanging information, or posting illegal content. |
| Membership & Participation | How users can engage with the content and other members | Public channels for viewing content, private groups with invite requirements, and moderated discussions. |
| Content Types | The specific types of content shared within these groups | Live video feeds from compromised cameras, hacking tutorials and tools, lists of vulnerable cameras, and malicious content. |
| Moderation & Regulation | Measures to maintain order and compliance. | Absence of moderation, content guidelines and rules to prevent abuse, or self-moderated communities. |
| Geographic Targeting | Groups or channels that may be localized in a specific region. | Channels associated with countries or regions like "Korean ipcam," "ipcam family,". |
| Technical Infrastructure | The technologies and methods used to carry out activities | Use of bots for automation, and links to third party sites for data. |
This structure allows a deeper exploration of how these groups function, how content is disseminated, and the overall risks involved.
The term "ipcam" itself is often found in various contexts on platforms like Telegram. This includes search queries, channel names, and content shared within groups. The term acts as a common identifier, allowing users to find and participate in these digital spaces.
These "ipcam" channels and groups are sometimes operated by unofficial service providers. These services may offer a variety of features, such as aggregated access to feeds, or tools and guides. These services exist on a platform level, and do not have any affiliation or endorsement. Users should be cautious about using them.
The ease of joining these groups and channels also raises concern, as does the content. These spaces often include links to illicit content, emphasizing the dangers of this digital world.
The core issue is not merely the existence of "ipcam" groups. It is the potential exposure of private data and the exploitation of security vulnerabilities. The lack of privacy on some digital platforms is an open invitation for malicious use.
The situation underscores the importance of taking all reasonable measures to secure your internet-connected devices and to exercise caution when browsing online. Stay informed, be vigilant, and protect your digital privacy.